It’s been years that everyone wants to kill him, but no one succeeds. Ever since computers have existed, the password has poisoned our daily lives. You have to make it complex without forgetting it, manage it in dedicated software, change it regularly, be careful not to pass it on to anyone, etc.
In 2018, the FIDO Alliance consortium thought it had initiated the beer, by proposing the FIDO2 standard. It relies on a fairly ingenious asymmetric cryptography mechanism to get rid of these cumbersome secret codes. But the mayonnaise didn’t take, and the password is still very much alive. The alliance now offers a new standard: the “Multi-device FIDO”, which has received support from the main technology giants (Google, Apple, Microsoft). Here are five questions to fully understand what it is all about.
Why was FIDO2 a failure?
On paper, FIDO2 is a great password alternative. The user who wants to connect to an online service must first proceed to an enrollment which consists in generating in his “authenticator” – a browser, a smartphone, a connected watch, etc. — a private key and a public key. The public key is transmitted to the service provider and the private key remains stored in the terminal. When the user wants to connect, he sends an authentication message signed with the private key to the service provider, who can verify the signature with the public key. That’s all. The big advantage is that there is no password to type and the risk of phishing is eliminated.
The problem is that there are very few online services that have implemented the FIDO2 standard. And this is logical, because this enrollment procedure is too tedious. As the generated private key is unique for each authenticator, it would be necessary to enroll for each terminal and each service. However, individuals handle many different terminals and renew them frequently. With three terminals and twenty departments, that theoretically makes… 60 enrollment procedures! And for each new terminal purchased, you have to stuff yourself with twenty new enrollments. We quickly preferred a centralized password manager in the cloud. You fill it once, and you’re done.
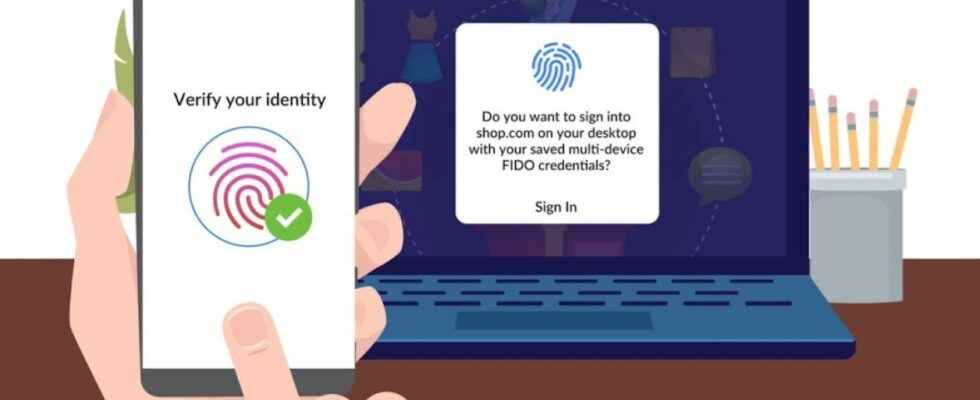
What answer does the FIDO Multi-device provide?
Two improvements should simplify the use of FIDO technologies at the level of the general public. The first is a “roaming” function, which will allow FIDO authentication to be used on a system that is not enrolled. Thus, the process can be relayed by Bluetooth to a nearby authenticator, typically a smartphone, where the user will validate the connection. The advantage is that the individual will no longer need to enroll each terminal. Ultimately, he can even settle for just one, provided of course that the systems are interoperable with each other.

The second novelty is the possibility of centrally saving the private keys at the authenticator supplier (ie the smartphone). If the latter is lost, the user can therefore easily regenerate his accesses, without going through new enrollment procedures.
The goal, in the end, is to have a system that is easy to manage. ” From a user experience perspective, this will be very similar to how one interacts with a password manager today when it comes to registering and securely logging into websites. . However, it will be much more secure, because the service server does not receive a password, but a public key », explains a spokesperson for the FIDO alliance.
How can you be sure that the terminals will be interoperable?
Authentication roaming via Bluetooth will be an integral part of the FIDO standard. All systems that implement “Multi-device FIDO” will automatically be interoperable. The good news, moreover, is that the three giants Google, Apple and Microsoft have announced that they will integrate this new authentication technology into their platforms. We can thus hope that Android, Windows, iOS and macOS systems are all interoperable at the roaming level. This would cover almost the entire consumer computing market.
To date, however, no deadline has been given. We also don’t know if service providers will finally take the plunge and adopt FIDO on their side. This is not self-evident, because the platforms have to be adapted. The inertia is likely to be strong, because it is a non-negligible investment.
Also see video:
Is multi-device FIDO as secure as FIDO2?
No. What we gain in terms of ease of use, we lose a little in terms of security, because the two new features also introduce two new risks. From now on, it will be necessary to trust the computer giants for the safeguard of the private keys. The fact that they are stored centrally also risks whetting the appetites of hackers… or intelligence agencies. Also, how will these private keys be stored at Google, Apple and Microsoft? Will they implement end-to-end encryption like most cloud password managers do? For now, we don’t know.
The second new risk is the relaying of the authentication procedure via Bluetooth, as it creates a new attack surface. However, the alliance minimizes this risk. On the one hand, this takes place in a context of proximity. On the other hand, the underlying FIDO protocol “does not depend on Bluetooth security properties for the security of the authentication procedure. Conversely, it uses standard cryptographic functions at the application layer to protect the data.explains the consortium.
What happens if I change ecosystem?
This will probably be the big downside of this whole construction, because a priori private key backups will not be interoperable from one ecosystem to another. With Multi-device FIDO, the idea is to use your smartphone as a means of access to all services. In fact, the private keys will therefore be saved either at Google or at Apple. But nothing says there will be a gateway from one ecosystem to another, and the FIDO alliance site suggests the opposite. Therefore, the day the user replaces his Android smartphone with an iPhone, it is likely that he will have to redo all the enrollments. Whereas with a password manager, this problem does not exist.