Hackers are currently hijacking the Windows Quick Support feature to gain access to their target victims’ computers by contacting them by phone… and presenting themselves as Microsoft technical support!
Computer threats are constantly evolving and we must constantly be extra vigilant to protect ourselves against new scams and hacking techniques developed by malicious actors. More than software and hardware security flaws, which are regularly corrected by manufacturers and developers through updates of their products, it is manipulation attacks which constitute the greatest danger for most users. By playing on a mixture of fear, urgency and persuasion, attackers trick their target into revealing sensitive data, such as identifiers or secret codes, and even manage to gain full access to the their victim’s computer, to install dangerous software.
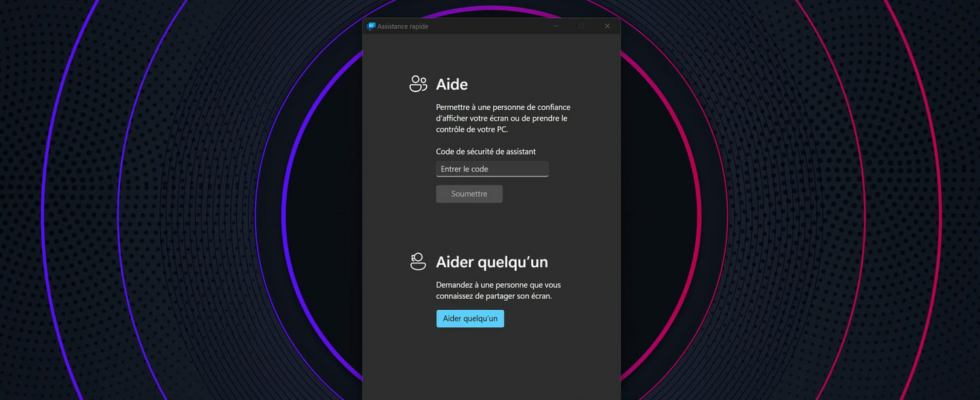
This is exactly the method currently used by a group of hackers targeting Windows users: they contact their targets by phone, posing as members of the company’s IT team or even technical support. Microsoft, in order to push their victim to give them access to their computer via a perfectly legitimate Windows tool, the Quick Assistance function.
Windows Quick Support: A hack based on manipulation
The Microsoft Threat Intelligence team, the group of people responsible for detecting and analyzing computer threats within the Redmond firm, recently published a safety note following the discovery of the malicious use of a Windows function, QuickAssist or Rapid Assistance, by the hacker group Storm-1811, via a social engineering technique called vishing. This name, contraction of vocal And phishing and which can be translated as voice phishing in French, refers to the act of contacting a potential target by telephone and pushing them to reveal sensitive information or to carry out actions compromising the security of their computer devices. The Quick Assistance function is a Windows tool that allows you to give a third party remote access to your computer in order to obtain help or resolve problems. This is a very practical function for remote troubleshooting but which obviously presents risks if used by a malicious person.
In this case, the attackers start by flooding their target’s email with unwanted emails, before calling them on the phone posing as their company’s IT department or even Microsoft technical support, and offering them their help in remedying the spam problem. Trusted, the victim is then invited to give access to their computer via the function Fast support of Windows, using a code provided by the attacker himself, which arouses less suspicion than a request to transmit a password. Once access is gained, the hackers then start running various scripts, which download and install various malware, to monitor the computer’s network activity, read the screen, record keystrokes and, at the same time, ultimately encrypts user data in order to demand a ransom. Potentially dramatic consequences therefore.
Windows Quick Assistance: recommendations to limit risks
Although this type of attack primarily targets businesses, which are most likely to hold sensitive data and pay ransoms, individuals are not entirely immune. In either case, Microsoft makes some recommendations to limit the risks of intrusion and compromise of its Windows devices using this method. The first and most obvious is to simply block or completely uninstall the Quick Support feature on computers where it is not used. In a professional computer park, this uninstallation will be done directly by the service concerned, but you can perfectly remove the Quick Assistance function yourself on your personal computer if you do not need it. On Windows 11, go to Settings > Applications > Installed applicationsfind the tool Fast support in the list and uninstall it like any application.
Then, when it comes to an attack by manipulation, the best defense remains training and user awareness of social engineering techniques. Scams based on usurping the identity of a person or an institution claiming to offer you their help have become legion: fake bank advisors who warn you of fraudulent movements on your account, fake police officers who ask you for help. the payment of alleged fines or false technical assistance which offers you to solve an annoying problem on your computer, all these methods are based on the same principle, to deceive your vigilance.
In the case of fake computer assistance, a good principle is to never give remote access to your computer to a person if you have not initiated the communication yourself and, when possible, to give this type access only to people you know physically. If you have initiated remote access and are in any doubt, immediately and without warning cut off the current connection and report the incident to the relevant services without delay. No one will blame you, quite the contrary: your colleagues in the IT department will always prefer an excess of caution to a potentially catastrophic intrusion into the company’s information system!