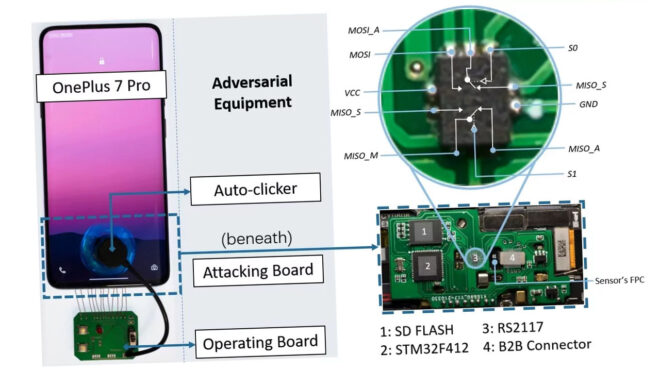
Android smartphones often come up with many security vulnerabilities due to the software basis. This time we have a hardware process.
For Android smartphones, Play Store-based application risks are often brought up. is coming. However, the open nature of Android also presents other problems. For example BrutePrint A new attack method called It exploits a vulnerability that allows unlimited fingerprint attempts on Android phones. For this attack, physical access to the phones is required first. Afterwards, you only need the hardware that you can see above for $15. After these two conditions are met The attack on the phones’ built-in fingerprint sensor begins. The prepared infrastructure makes use of a fingerprint database and unlocks the phones. trying to get through with lots of tries. Unlike passwords, which, as transmitted, require an exact match, fingerprint authentication determines a match using a reference threshold. Therefore, to bypass the fingerprint lock, it is sufficient to find a match close enough to another fingerprint in the database.
YOU MAY BE INTERESTED
Security researchers who found this attack method Xiaomi Mi 11 Ultra, vivo X60 Pro, OnePlus 7 Pro, OPPO Reno Ace, Samsung Galaxy S10 Plus, OnePlus 5T, Huawei Mate 30 Pro 5G, Huawei P40, iPhone SE And iPhone 7 explains what they have done. Bypassing the fingerprint on the phones listed above, according to researchers ranged from 40 minutes to 14 hours. The system did not work on iPhones. This is due to the fact that the iOS operating system encrypts data, while Android does not. The names behind BrutePrint say mitigating this serious threat will require a concerted effort between smartphone manufacturers and fingerprint sensor manufacturers to curb the process. He states that some things can be done in the Android operating system as well.